Healthcare providers are searching for simpler ways they can communicate with patients. It can be tedious to schedule all communication in person or over the phone, so medical professionals are looking for another way. Email has become a popular form of communication for those in the healthcare industry, but there are questions about its legality […]
VersaTrust Blog
VersaTrust has been serving the Texas area since 1997 , providing IT Support such as technical helpdesk support, computer support and consulting to small and medium-sized businesses.
Intel processors are having a Meltdown while AMD and ARM are being attacked by a Spectre. Is a James Bond villain making our computers freak out? No, it’s a new vulnerability found within these processors that affects Windows PCs, Linux, Mac, and even Android phones. A fix has been identified, named KAISER, and all the […]
Two critical vulnerabilities were found in Intel chips that could result in a malicious attacker stealing your data, such as photos, emails, documents, browsers, and password managers. How can this affect you? The vulnerabilities called “Meltdown” and “Spectre,” can affect nearly every system built since 1995. This includes computers and phones. A proof-of-concept code was tweeted out […]
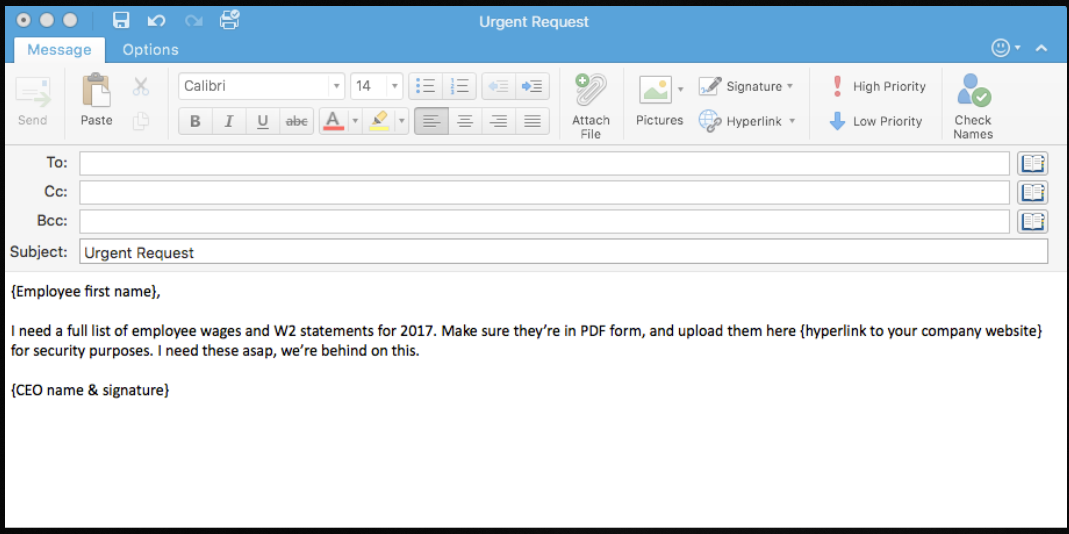
W-2 Phishing season is about to begin – without the right IT security services, your business will be left vulnerable. You and I know that effective communication with co-workers and clients is crucial, but are you sure your employees are practicing safe email and messaging conduct? If you don’t already have the best technical security […]
If you run a business, chances are that you’ve thought about moving to an online productivity suite. The two most popular in recent years is Google’s G Suite and Microsoft’s Office 365. Touted as “innovative” and “the next big thing,” Microsoft’s productivity suite is a revolutionary concept when it comes to operating systems and computing. […]