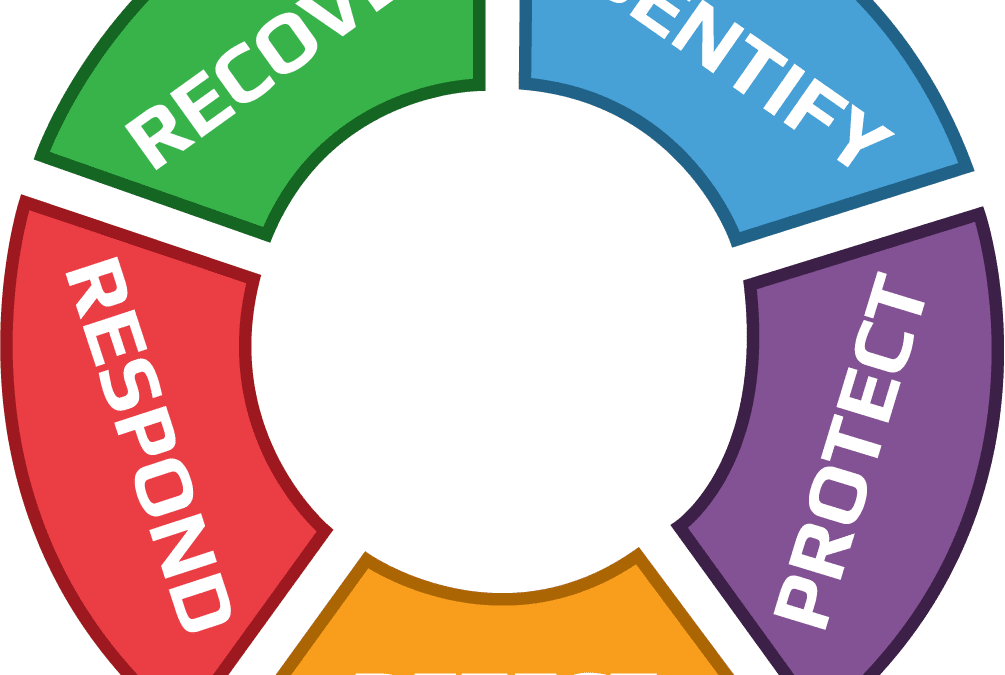
When we think of hygiene most of our tasks like brushing our teeth, brushing our hair, washing our faces are ingrained into our day-to-day activities. You likely don’t even think of them; you just do them. Does your team view cyber hygiene the same way? If not, your cybersecurity strategy and practices could be lacking. […]
VersaTrust Blog
VersaTrust has been serving the Texas area since 1997 , providing IT Support such as technical helpdesk support, computer support and consulting to small and medium-sized businesses.
If your business was targeted by a successful cyberattack, do you have a plan for recovery? Would you be able to recover? Cybersecurity insurance helps companies protect their brand against the financial and reputation losses that are associated with successful data breaches, ransomware, malware, phishing, and other types of cyberattacks. And this type of insurance […]
Revision 3, or Rev. 3, for 800-171 by the National Institute of Standards and Technology (NIST), is expected to be published early in 2024. The update introduces significant changes, including new requirements. Contractors and vendors who wish to do work with the Department of Defense (DoD), as well as these contractors’ vendors and subcontractors, must […]
Even if you specialize in cybersecurity, your in-house IT likely will not meet strict government standards. If you aren’t NIST compliant, for instance, most bids will be rejected automatically. IT compliance isn’t optional anymore – you need to be compliant with key security standards, and the best way to do this is to partner with a […]
By this point, all companies in the defense sector (contractors and subcontractors) know they need to adhere to CMMC compliance requirements. With the U.S. Department of Defense and NIST updating guidelines, it’s vital to understand what changes are coming and when. Heading into 2024, clarity on this timeline becomes crucial for compliance planning. We’ve mapped […]
Businesses that deal with federal contract information (FCI) and controlled unclassified information (CUI) know that CMMC compliance requirements have to be a top concern. The Department of Defense (DoD) developed the CMMC standards to ensure that the contractors with access to this sensitive information have the security systems to safeguard the data. The CMMC audit […]
The Cybersecurity Maturity Model Certification (CMMC) compliance requirements were recently updated to simplify and clarify the security standards organizations contracting or subcontracting for the Department of Defense must abide by. By 2026, most businesses seeking to contract with the DoD or subcontract with a DoD contractor will be required to obtain certification that confirms their […]
Fort Worth — the most typically Texan of all Texas cities — began as a tiny outpost on a lonely frontier. Today, this metropolitan area of more than 900,000 people blends its cattle and oil heritage seamlessly with an ever-growing, diverse array of new businesses and industries. When it comes to safeguarding your business in […]
In today’s fast-paced digital world, IT services play a crucial role in helping organizations manage their data efficiently and securely. As data becomes an increasingly valuable asset, the need for advanced tools and technologies to manage and analyze it is growing rapidly. Enter artificial intelligence (AI). Having reached a tipping point in adoption, it is […]